If you’re on the path of starting to use a VPN or proxy and are confused about which one to choose, then today we’re here to give you a better understanding ..
affect everyone from ordinary people like you and me to multi-billion-dollar corporate giants. We all may think about what could save us from cyberattacks if the business-world mammoths can’t be saved. Well, staying protected in the digital world isn’t nuclear science, and small steps such as using a VPN or proxy server can increase your online safety by many folds.
is another commonly used protocol that helps in securing the connection between the device and the proxy server. With an HTTPS connection enabled/established, the request/response data are encrypted hence allowing to maintain security and privacy while browsing the web. Similar to HTTPS, SSL and TLS are two other cryptographic algorithms utilized to ensure that the data transmission of data between the source and a destination remains encrypted and secure. TLS is basically the successor to the SSL protocol, however, it’s backward compatible as well. SSL /TLS : Protocols such as , SSL/TLS, etc. are also utilized by VPN services to provide data protection.
In symmetric encryption, a secret key is generated and is confidentially shared between the sender and the receiver. The message being transmitted is then encrypted using the secure key by the sender, whereas the receiver can use the same shared key to decrypt the message on their end. AES-128 and AES-256 are two of the commonly used symmetric encryption algorithms for VPN services.
South Africa Latest News, South Africa Headlines
Similar News:You can also read news stories similar to this one that we have collected from other news sources.
 Google is investing $2 billion into Anthropic, a rival to OpenAIThis escalate Big Tech's proxy fight over the next big platform shift.
Google is investing $2 billion into Anthropic, a rival to OpenAIThis escalate Big Tech's proxy fight over the next big platform shift.
Read more »
 Orca-strated Chaos: Understanding a Summer of Orca DramaThis summer has been full of orca news stories, from boat-bashing, to interspecies adoption (or kidnapping), to harassing other animals for no obvious reason.
Orca-strated Chaos: Understanding a Summer of Orca DramaThis summer has been full of orca news stories, from boat-bashing, to interspecies adoption (or kidnapping), to harassing other animals for no obvious reason.
Read more »
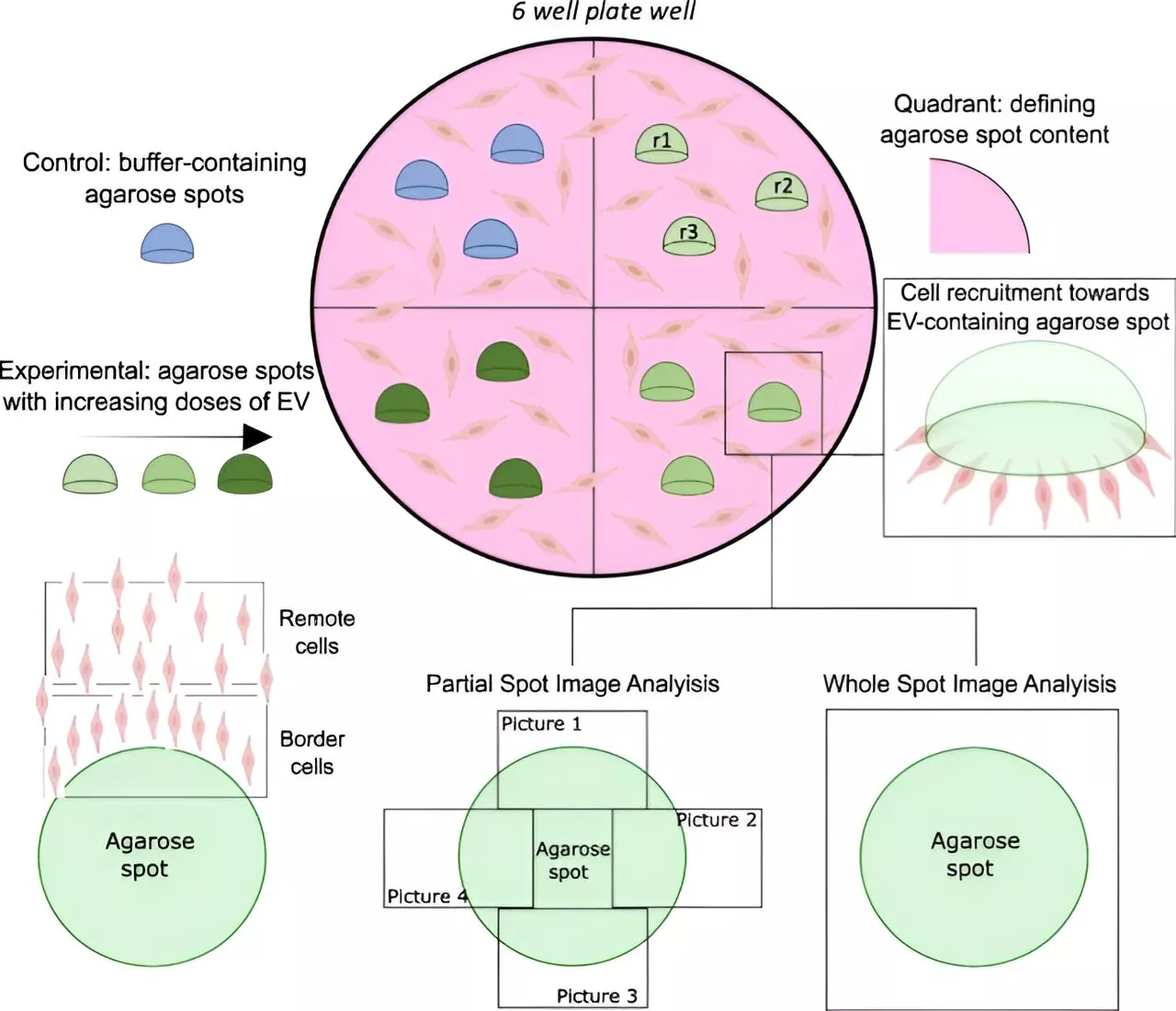 Agarose-based method shows potential in understanding extracellular vesicles' role in cancer metastasisA collaborative study led by researchers from Germans Trias i Pujol Research Institute has revealed the promising possibilities of using an agarose spot migration assay to examine the ability of extracellular vesicles to attract other cells in a controlled environment. The study has been recently published in the journal BMC Biology.
Agarose-based method shows potential in understanding extracellular vesicles' role in cancer metastasisA collaborative study led by researchers from Germans Trias i Pujol Research Institute has revealed the promising possibilities of using an agarose spot migration assay to examine the ability of extracellular vesicles to attract other cells in a controlled environment. The study has been recently published in the journal BMC Biology.
Read more »
 Understanding ERC-4337 and the Future of Account Abstraction in EthereumUnderstanding ERC-4337 and the Future of Ethereum User Experience: Account Abstraction
Understanding ERC-4337 and the Future of Account Abstraction in EthereumUnderstanding ERC-4337 and the Future of Ethereum User Experience: Account Abstraction
Read more »
2024 Tesla Model 3 Highland Deep Dive: Understanding the TechThink the new Model 3 Highland is just a midcycle facelift? There’s more to Tesla’s updated and upgraded entry-level electric car than meets the eye.
Read more »
 Understanding just how absurd A.J. Brown's performance has beenA.J. Brown has been putting up historic numbers for more than a month straight.
Understanding just how absurd A.J. Brown's performance has beenA.J. Brown has been putting up historic numbers for more than a month straight.
Read more »
