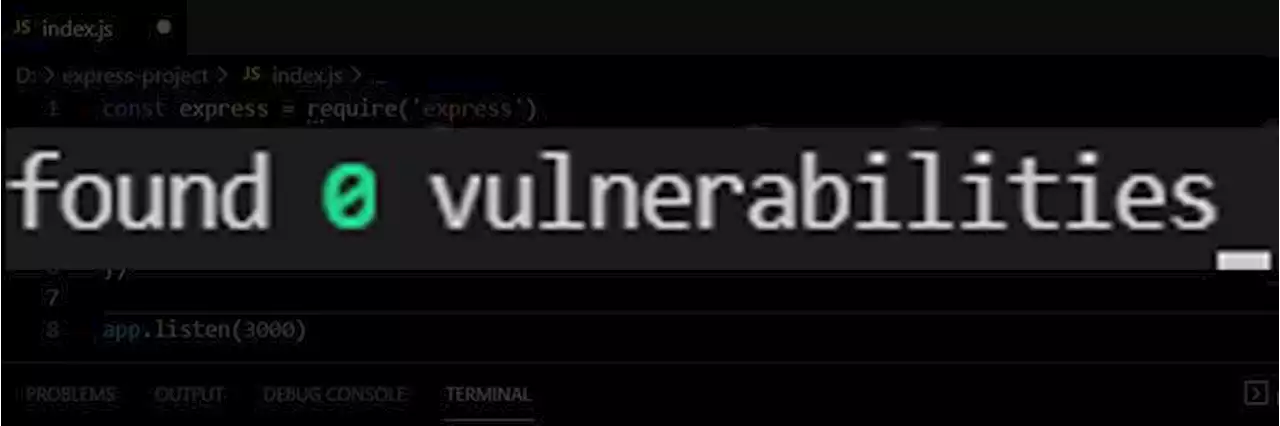
'Securing your NodeJs Express Application — Part 1' nodejs security
Amazon is right on track to surpass Walmart as the biggest USA retailer in 2022. Amazon’s GMV in 2020 mounted 41 percent year by year to around $316 billion. Alibaba acquiring physical supermarkets and Target buying out an online delivery platform appears a further collision of business strategies.
. The best practice is to use the latest stable packages to mitigate such vulnerabilities. You can use thecommand to find out known vulnerabilities in your Nodejs application. Then you can fix them by running theSecure your HTTP Headers Proper HTTP headers can prevent security vulnerabilities like Cross-Site Scripting, Click-jacking, Packet sniffing and, information disclosure. It’s better not to use Express with its default HTTP headers. Try theconst express=require; const helmet=require;const app=express;app.use);// ...Hackers should find a way into your application and, request parameters are their first choice.
South Africa Latest News, South Africa Headlines
Similar News:You can also read news stories similar to this one that we have collected from other news sources.
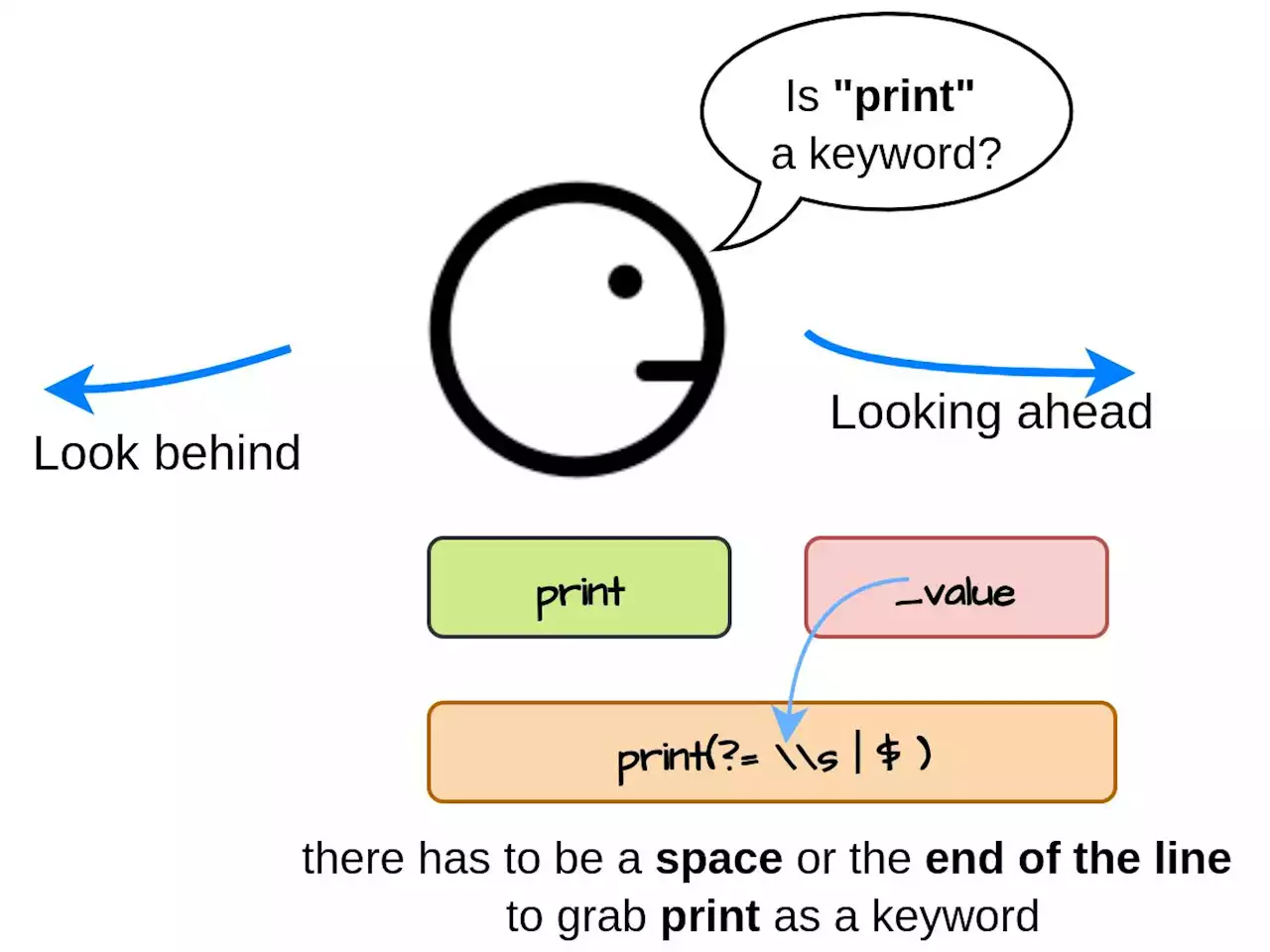 Build Your Own Programming Language Part III: Improving Lexical Analysis with Regex Lookaheads | HackerNoon'Build Your Own Programming Language Part III: Improving Lexical Analysis with Regex Lookaheads' lexicalanalysis regex
Build Your Own Programming Language Part III: Improving Lexical Analysis with Regex Lookaheads | HackerNoon'Build Your Own Programming Language Part III: Improving Lexical Analysis with Regex Lookaheads' lexicalanalysis regex
Read more »
 Bullieverse: Building a Metaverse Beyond Gaming | HackerNoonDuring the Non-fungible Conference, Hackernoon got an exclusive interview with Arunkumar Krishnakumar, who shared insights on his new project, Bullieverse.
Bullieverse: Building a Metaverse Beyond Gaming | HackerNoonDuring the Non-fungible Conference, Hackernoon got an exclusive interview with Arunkumar Krishnakumar, who shared insights on his new project, Bullieverse.
Read more »
 Poll Finds About 1 in 3 Professionals Use Cannabis at Work | HackerNoon'Poll Finds About 1 in 3 Professionals Use Cannabis at Work' by seriouslyrick business futureofwork
Poll Finds About 1 in 3 Professionals Use Cannabis at Work | HackerNoon'Poll Finds About 1 in 3 Professionals Use Cannabis at Work' by seriouslyrick business futureofwork
Read more »
 'Welcome to the Era of Cyber-Education' | HackerNoonThe rise of the internet, and also its bubble, has enabled autodidacts to learn more than they ever could.
'Welcome to the Era of Cyber-Education' | HackerNoonThe rise of the internet, and also its bubble, has enabled autodidacts to learn more than they ever could.
Read more »
 A New Data Model for Bitcoin: U2R Method | HackerNoonSome say bitcoin's Stock-to-Flow models S2F and S2Fx are dead. I don't, but just in case 'they' are right, here's an alternative model.
A New Data Model for Bitcoin: U2R Method | HackerNoonSome say bitcoin's Stock-to-Flow models S2F and S2Fx are dead. I don't, but just in case 'they' are right, here's an alternative model.
Read more »
 Meme Coins That Still Have Market Traction in 2022 | HackerNoon'Meme Coins That Still Have Market Traction in 2022' by CryptoAdventure memecoins memetokens
Meme Coins That Still Have Market Traction in 2022 | HackerNoon'Meme Coins That Still Have Market Traction in 2022' by CryptoAdventure memecoins memetokens
Read more »