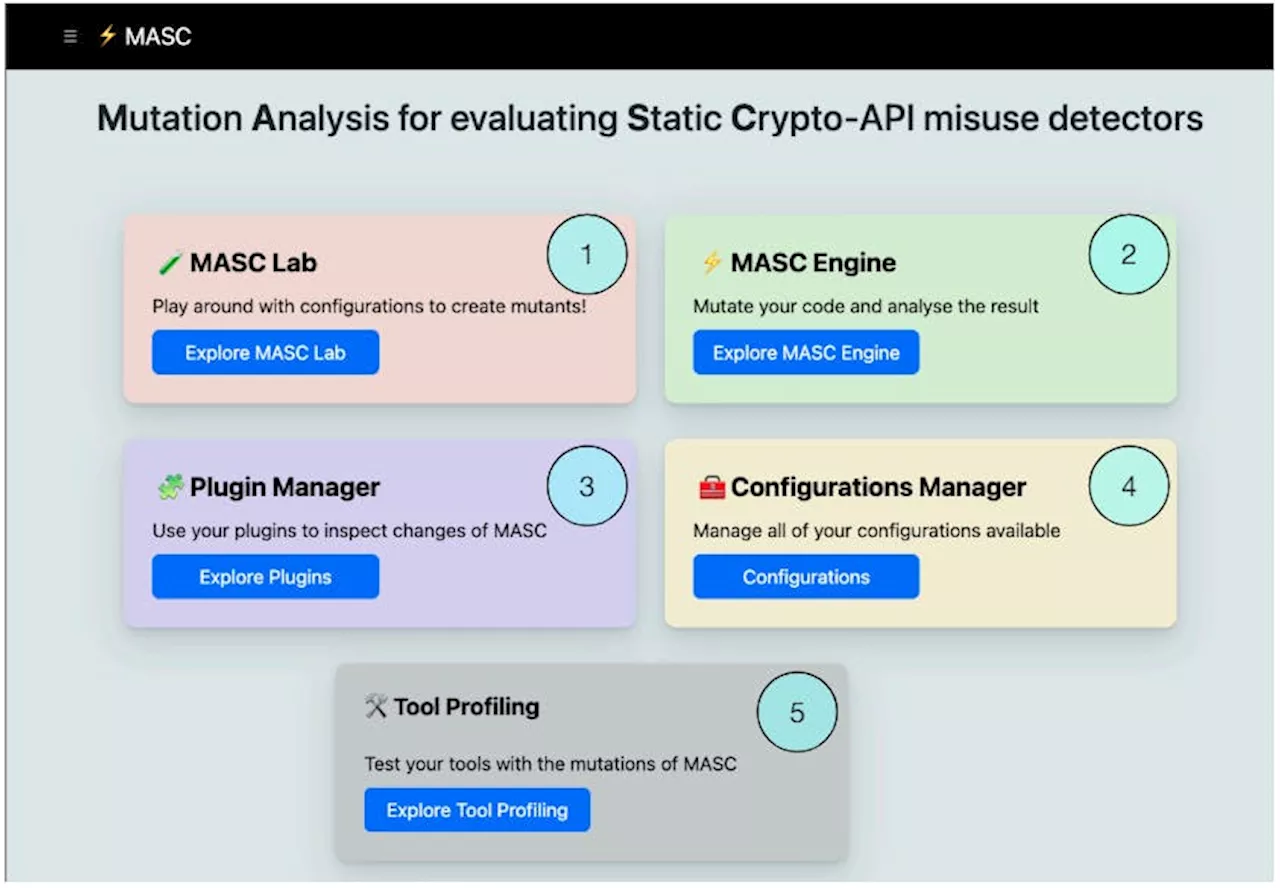
Learn how to use MASC via command line and web interfaces for testing and analyzing crypto-API misuses in software development.
Authors: Amit Seal Ami, Computer Science Department, William & Mary Williamsburg, Virginia, USA, and this author contributed equally to this paper ; Syed Yusuf Ahmed, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper ; Radowan Mahmud Redoy, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper ; Nathan Cooper, Computer Science Department,...
can be executed by providing a configuration file e.g., Cipher.properties using the command shown in Listing 4.
can be executed by providing a configuration file e.g., Cipher.properties using the command shown in Listing 4.
South Africa Latest News, South Africa Headlines
Similar News:You can also read news stories similar to this one that we have collected from other news sources.
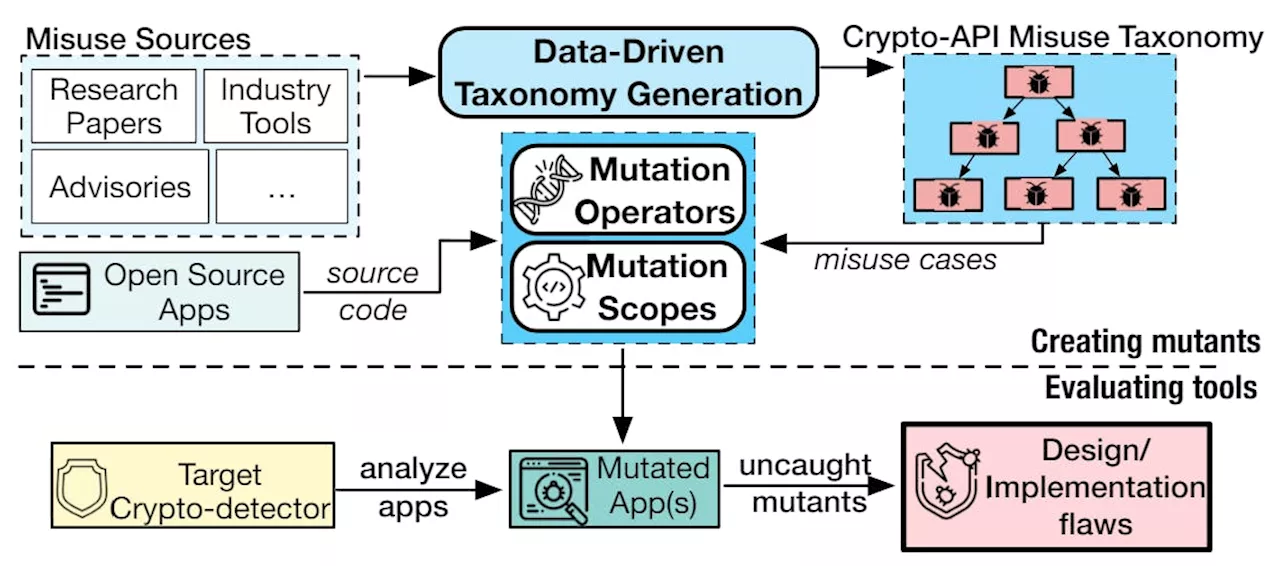 MASC: A Tool for Mutation-Based Evaluation of Static Crypto-API Misuse DetectorsLearn about MASC, an advanced tool designed for evaluating crypto-detectors, identifying crypto-API misuse, and enhancing software security.
MASC: A Tool for Mutation-Based Evaluation of Static Crypto-API Misuse DetectorsLearn about MASC, an advanced tool designed for evaluating crypto-detectors, identifying crypto-API misuse, and enhancing software security.
Read more »
 The Token Bucket Algorithm for API Rate Limiting in NodeJS: A Simple GuideLearn how to implement the Token Bucket algorithm in NodeJS for API rate limiting, controlling server usage with a simple and effective approach.
The Token Bucket Algorithm for API Rate Limiting in NodeJS: A Simple GuideLearn how to implement the Token Bucket algorithm in NodeJS for API rate limiting, controlling server usage with a simple and effective approach.
Read more »
 Strengthening IoT Security through Role-Based User Authentication FrameworksThis article briefly explains the contribution of role-based user authentication to IoT security.
Strengthening IoT Security through Role-Based User Authentication FrameworksThis article briefly explains the contribution of role-based user authentication to IoT security.
Read more »
 Building a User-Friendly Interface for Central Bank Digital Currency Applications: A Case StudyI share my experience in designing the interface of a retail CBDC application. Perhaps these technologies will soon compete with traditional banking
Building a User-Friendly Interface for Central Bank Digital Currency Applications: A Case StudyI share my experience in designing the interface of a retail CBDC application. Perhaps these technologies will soon compete with traditional banking
Read more »
 How Will Federal Cannabis Rescheduling Affect the Average User?There could be big changes to cannabis taxes and clinical research — but how will it impact the average dispensary shopper?
How Will Federal Cannabis Rescheduling Affect the Average User?There could be big changes to cannabis taxes and clinical research — but how will it impact the average dispensary shopper?
Read more »
 Building Ethical AI: How To Take A User-Centered ApproachSuccessful CIOs, CTOs & executives from Forbes Technology Council offer firsthand insights on tech & business.
Building Ethical AI: How To Take A User-Centered ApproachSuccessful CIOs, CTOs & executives from Forbes Technology Council offer firsthand insights on tech & business.
Read more »